Tor and mobile proxies

Tor– An effective non-commercial program that provides users with anonymous access to the Internet. It is able to redirect traffic between points of a distributed server network located in different parts of the world. As a result, the privacy of Internet connections and the hiding of personal data are ensured. But thanks to proxy servers, your work on the network will be completely classified – there are no traces left to trace.
Let's take a closer look at the features of this program. Let's dwell on the advantages of the joint work of Tor and proxy servers. Let's write out the step-by-step process of settings. We will show you where to buy reliable functional mobile proxies for working with Tor.
Thor features
Tor can be used as a standalone tool when working on the network, and can work in conjunction with a browser, in particular with Tor Browser based on Firefox, created to provide absolute anonymity of interactions on the Internet. The program encrypts traffic three times:
- The encrypted data stream is sent to the first server in the chain. Here the first layer of encryption is removed and the address of the second server becomes visible, to which the traffic is sent.
- The second server on the network decrypts another layer and sees the address of the third party in the chain, but does not know where the data came from and where it should end up as a result.
- The third server decrypts the last layer, and only it provides the user with access to the Internet. But, like the previous participants in the chain, it does not know the outgoing point.
Thanks to Tor, you will access the Internet from a new server computer every time. In this case, the browser will not save the history of visits, actions on the network. Unlike VPN, the program does not provide privacy, but the anonymity of browsing the Internet. But you need to understand that, despite the legality of the Tor program, its use may attract the attention of services that monitor the safety of working on the network. And to prevent this from happening, you must use it in conjunction with a proxy server.
What you can get from sharing Tor and mobile proxies
Working with the Tor program through mobile proxies will be useful to all Internet users without exception. For ordinary people, it will provide a high level of anonymity in the network and not only:
- no one will know what sites you visited: it is impossible to identify traffic, extract at least some information from your data;
- does not identify your real location, computer address (IP address and geolocation are hidden by replacing real data with the technical information of the last proxy server in the chain);
- will protect traffic from providers, legal restrictions, dangers when using public WiFi hotspots;
- allows you to bypass regional blocking, censorship;
- ad trackers will be blocked by automatically resetting cookies on shutdown;
- multi-level encryption combined with an HTTPS proxy provides guaranteed protection against unauthorized access, etc.
Users whose professional activities are related to the Internet will receive even more benefits: affiliates, SEO and SMM specialists, marketers, etc. Thanks to the combined use of Tor and mobile proxies, you will be able to solve multiple personal and professional tasks on the Internet, without leaving any traces. You just need to make a number of settings correctly.
Sequence of setting up mobile proxies for working with Tor
Setting up a mobile proxy to work with Tor will take a few minutes. You will need to do the following:
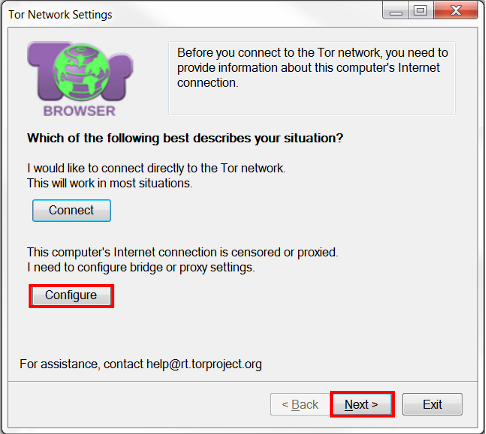
- Launch the Tor program. In the window that opens, we find the "Configure" button. Click on it, and then – on the "Next" button at the bottom of the window.

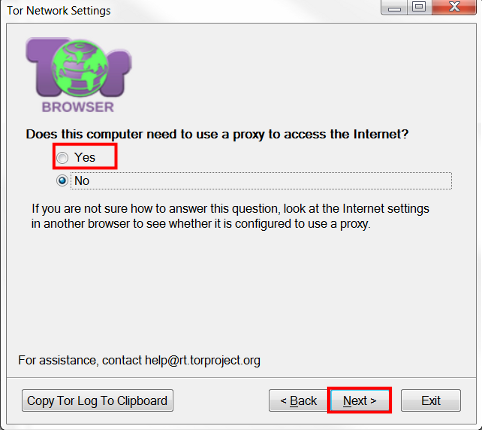
- In a new tab, you will see the question: "Will this computer use a proxy to access the Internet." We answer it positively by clicking on "Yes". To continue the settings, click on the "Next" button. at the bottom of the window.
 < /li>
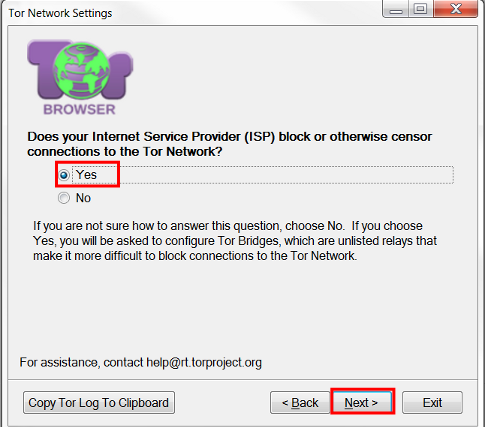
< /li> - A new window opens asking "Does your ISP block or otherwise censor connections to TorNetwork?" Here you also need to answer "Yes" and switch to a new tab by clicking the "Next" button.

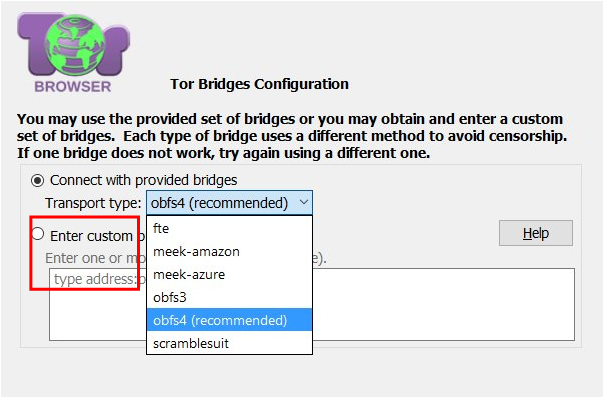
- In a new tab, you must specify the type of proxy server through which work will be performed in the future. Here, from the proposed list, select the HTTPS option.

- Open the Tor Browser browser, find the onion icon in the command line, click on it.

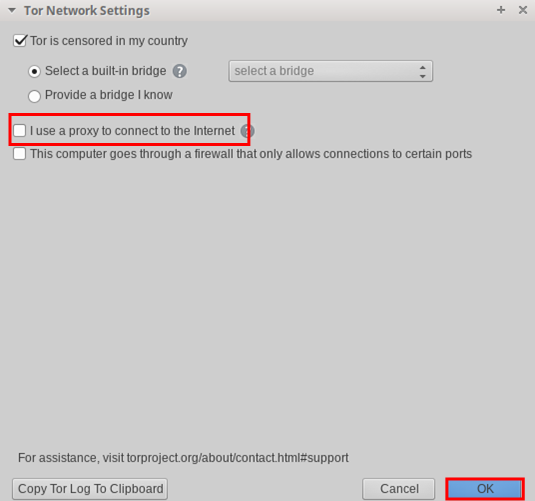
- In the window that opens, we do not remove the basic marks, but additionally check the box next to the inscription "I use a proxy to connect to the Internet". Click on the "OK" button in the bottom right corner of the window.

Everything. This completes the settings. Now it is impossible to identify either you when working with the Internet, or to establish the fact that interaction with the network is carried out through the Tor program. But you need to understand that the efficiency, stability and security of all your subsequent actions largely depend on which mobile proxies are used in your work. Let's devote a couple of moments to this issue.
The best mobile proxies for working with Tor
For working with software Tor, the optimal solution is – private mobile proxies. Yes, the market today also offers free analogues that are freely available on the network. But the efficiency of their work is very low, because a huge number of people can use the same server at the same time. This will affect security, interaction speed, and increase the risk of blocking.
Would you like to avoid these problems? Buy personal high-speed mobile proxies with wide functionality from the MobileProxy.Space service. You get a personal channel with unlimited traffic, instant connection and guaranteed anonymity of work. Take advantage of the offer and see for yourself.