Unirest Library: HTTP-сlient Briefing

Those who are related to programming and IT-technologies in general probably know that special libraries, the so-called HTTP-clients, are used to interact between servers and sites. Their job is to send requests and receive responses. We will get acquainted with one of these libraries today. This is a lightweight Unirest product. Today it is available to users in several languages. It was created by the Kong company and is still serviced by it. A unique feature of this – support for various HTTP methods, in particular GET, POST, DELETE, HEAD, etc. (request types API). You can easily add them to your applications, which is especially true for relatively simple user cases.
Now let's get acquainted with the Unirest library in more detail, highlight its main advantages. We will tell you how to install it and put it into operation. We will also dwell on how to ensure the stability and security of the network, unlimited opportunities for testing software products using mobile proxies.
Unirest Library Features
Today, Unirest can be attributed to one of the most popular JavaScript and PHP-libraries. It can be used to quickly and easily extract the necessary data from the Internet. Among its main advantages are:
- support for all types of API-requests and, accordingly, HTTP-methods;
- fast, stable and efficient operation, even with a fairly high load;
- using the easiest way to transfer files through the server.
Now let's move on to how the Unirest library is used to implement the RestAPI using the PHP-programming language. Let's make a reservation right away that here it is more used not as a server part, but as a client part. Another HTTP-client option that deserves attention is – library Axios. Perhaps her tools will be useful in your work.
How do I install the Unirest library?
Your user device must have PHP 5.4+ and cURL installed before you can install the Unirest library. Is there such a thing? Then you can proceed to the installation itself. Here, no one should have any problems. It will be enough to use Composer – a manager for connecting and managing third-party data packages or libraries in your PHP project. Here in the corresponding window you will need to enter only a single command: composer require mashape/unirest-php.
After executing it, the latest version of the Unirest library will be directed to your device. You will only have to agree to its installation. Please note: if you plan to use the untagged version of the library in your future work, then you should use another command, in particular: composer require mashape/php-test-reporter dev-master. After downloading the library via Composer, you will need to connect via «require_once». You are interested in the "autoload.php" file.
How to work with the Unirest library?
Before you start working with the Unirest library, you need to have a good understanding of its distinctive features. In particular, we highlight:
- the presence of a large number of utility methods for calling requests: GET, CONNECT, HEAD, PUT, POST, DELETE, TRACE, OPTIONS, PATCH;
- support for the gzip compression and recovery utility;
- the ability to quickly and conveniently set the timeout;
- support for form, file upload, custom objects, and custom headers for each individual request;
- Perform automatic parsing of JSON into a personal object.
An example of sending the simplest request is shown in the picture:
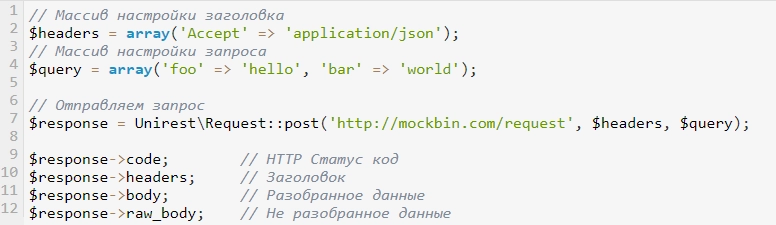
As you can see from the example, in it we did not just send a request to the Internet resource. Before that, we created two separate arrays: one – for the header, but the second – directly for request data. We also sent a POST request, and the response we received was stored in the "$response" variable.
If you are faced with the task of sending data as an array of JSON parameters, then here you will need to run a slightly different command, in particular:
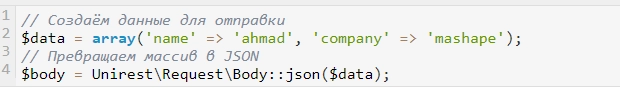
Here you've created an array of JSON data from a regular array specifically to trigger the upload. If you plan to use a JSON data array in your work, then follow these recommendations:
- The Content-Type request header must contain "application/json";
- Variable data will be handled via «json_encode(argument)» with default argument values;
- if the JSON extension is not available, the system will throw an error.
Note that we've used POST requests throughout the examples above, but we've already mentioned that the Unirest library can handle other kinds of requests as well. In practice it will look like this:
- Unirest\Request::get($url, $headers = array(), $parameters = null)
- Unirest\Request::post($url, $headers = array(), $body = null)
- Unirest\Request::delete($url, $headers = array(), $body = null)
- Unirest\Request::put($url, $headers = array(), $body = null)
- Unirest\Request::patch($url, $headers = array(), $body = null)
Actually, that's all. As you can see, the Unirest library is quite simple to use and undemanding to system resources. But still, when working with it, as well as with any other actions on the network, it is recommended to additionally take care of your own protection against unauthorized access, hacker attacks and anonymity. An additional connection to the work of mobile proxies will help to ensure this.
Mobile proxies for secure Internet browsing and the Unirest library
Any user's actions on the network, regardless of whether it is a professional activity or the work of an ordinary person, are always fraught with potential danger. The fact is that any resource that you visit will determine the IP-address of the device from which the visit was made. Accordingly, it will be possible to determine the geolocation. And this at times increases your vulnerability to all kinds of malware, unauthorized access. Mobile proxies – this is a kind of intermediary that will replace your technical parameters with your own. This ensures:
- complete anonymity and connection security: your unique IP-address on the network will be invisible;
- bypassing regional blocking, gaining access to sites from all over the world, the ability to test software in certain geographic conditions;
- higher connection speed: provided by the operation of mobile proxies on the technical capabilities of mobile network operators, as well as data caching;
- Stable and efficient work in multi-threaded mode using automated software without the risk of getting banned by anti-fraud systems.
But, you need to understand that such functionality is inherent only in private servers. Free proxies, which today everyone can find on the net in free access – not an option. The fact is that everyone can use them, which in itself significantly reduces the level of security. In addition, the speed of their work will be very low. We must not forget about such a moment as the presence of a "black list" IP-addresses into which the system enters all the addresses of free servers that it identifies. And this means that an attempt to enter from them will immediately be blocked. What kind of work stability can we talk about then?
The best mobile proxies from MobileProxy.Space
By selecting mobile proxies from the MobileProxy.Space service, you get:
- Personal dedicated channel with unlimited traffic. Only you will be present on the channel.
- The use of real IP-addresses from GSM operators in the work. Today, our pool already has almost 1 million available options and their number is increasing every day.
- The ability to configure a timer through your personal account to automatically change IP-addresses at intervals from 2 minutes to 1 hour. It will also be possible to change addresses forcibly, by reference.
- You can configure authorization by IP-address, eliminating the need to constantly enter your login and password.
- Simultaneous work on HTTP(S) and Socks5 protocols. Connected via parallel ports.
To learn more about the features of mobile proxies, follow the link https://mobileproxy.space/en/user.html?buyproxy. It is also possible to take advantage of free testing for two hours without restrictions on access and traffic.