Connecting private mobile proxies to Epic Privacy Browser

The article content
- Getting to know epic privacy browser
- Main functions of epic privacy browser
- What are the disadvantages and limitations of epic privacy browser?
- So is it worth trying epic privacy browser in work?
- The sequence of actions for setting up private proxies in epic privacy browser
- The best proxies for connecting to epic privacy browser
- Let's sum it up
Today, the issue of ensuring safe and confidential work on the Internet is very relevant for most users. The modern market offers many solutions in this area. So, you can delete the history of your visits every time you close the browser, you can use a special incognito mode. Also, one of the available solutions is to install the Do Not Track plugin, which allows you to remove advertising tracking and use a proxy server to hide your real IP-address from the system. But there is another effective, but at the same time simple and easy-to-use solution - Epic Privacy Browser.
This is the tool that will provide reliable protection of private data and a number of additional functionalities without any complex settings, time and money. Looking a little ahead, we note that this product is completely free to use and anyone can download it. Also, with its help, you can bypass regional restrictions and access sites blocked in your region. That is, by betting on Epic Privacy Browser, you will ensure yourself absolutely anonymous surfing on the network without any risks and restrictions.
As part of today's review, we will dwell in more detail on what this browser is, highlight its functionality, advantages and disadvantages. We will tell you how to connect your own private proxy servers to Epic Privacy Browser so that you can work online without any risks.
Getting to know Epic Privacy Browser
The first thing I would like to draw your attention to is that, like all other popular browsers today, Epic Privacy Browser runs on the Chromium engine. This is what makes it visually similar to the popular Google Chrome. This means that each of you will be able to figure it out and adapt to work with minimal time and effort. At the same time, it also has a Russian-language interface, albeit with the exception of the welcome page.
The browser itself has a minimal set of plugins, due to which there is a high download speed, minimal hardware requirements. Here, the load on the central processor and system memory will be very insignificant. In addition, this browser blocks third-party cookies. In order to ensure anonymity of work and bypass regional restrictions, it will be enough to simply click on the corresponding icon and switch the work to the proxy server mode.
In addition to everything, Epic Privacy Browser blocks advertising channels, including social network plugins, web analytics systems, whose responsibilities include tracking user activity on the network. That is, you simply enter the address in the database line that is stored on your computer and go directly to the site itself, but this information will be absent in the browser itself.
Today, Epic browsers are supported by devices running on Windows and Mac OS X operating systems. Relatively recently, a separate version for Android appeared on the market. In operation, this solution will be useful to a wide range of user audiences:
- individuals wishing to keep their actions on the Internet confidential;
- representatives of non-profit organizations, as well as various business areas that care about their own security when working online;
- representatives of services that a priori must maintain their incognito when interacting with the World Wide Web, such as police representatives, journalists, government officials, politicians;
- large corporations that would like to maintain the confidentiality of their own developments and personal data of clients, to ensure reliable protection from any unauthorized access;
- representatives of such professions as arbitrageurs, Internet marketers, SEO and SMM specialists, software developers and testers, etc.
The fact is that the same incognito mode or private browsing, which many users rely on, will not provide reliable protection from tracking. More extensive and professional solutions are needed here. This is exactly what Epic Privacy Browser offers. As soon as you launch this browser and activate the proxy, the system automatically hides your real IP address, encrypts all DNS requests and even views. It will block the tracking scenario, as well as any attempts by third parties to access your information.
To ensure effective bypass of regional restrictions, Epic Privacy Browser also has different geolocations. So, today it provides GEOs of 8 countries of the world: USA, Canada, Great Britain, Germany, France, Netherlands, Singapore, India. With their help, you will be able to work with such popular services as Netflix, YouTube, Hulu, Spotify, Pandora and many others without any restrictions. In addition, the browser developers claim that when working through their search engine, all your information will be reliably hidden not only from the system itself, the Internet provider, but also from government agencies, as well as any other services that collect personal data. This also applies to search engines such as Google.
By default, Epic Privacy Browser does not save history. There is no preliminary DNS and web cache settings, third-party cookies. Even spelling is not checked in this service. As soon as you finish working with the browser, links to all those sites that you viewed, certificates and links related to Origin will be automatically deleted. As we said above, Epic Privacy Browser does not have a line for checking the url and entering the site address. There is no error tracking with subsequent output to an alternative page.
To start working with this browser, you just need to download the appropriate software. If you have already worked with the same Google Chrome, then you will not have any difficulties when interacting with Epic Privacy Browser, since everything is very similar here. The home page of this search engine includes 8 panels on which you can place those Internet resources that you most often use in your work, which will provide faster and easier access to them. But, to tell the truth, you will only be able to add 6 favorite sites here, since 2 available panels will already be automatically occupied. One of them will redirect you directly to the page with the browser user guide, while the second one leads to safe search.
In principle, something similar is implemented in the same Google Chrome, but with the difference that here the system fills in all the panels with the most popular sites automatically. That is, it monitors the sites you visit, and then independently adds them to the corresponding windows. But since Epic Privacy Browser does not monitor all the resources you visit, it does not have such information, which means you will have to enter all these sites manually. In addition, the number of blocked trackers and cookies will be immediately displayed on the home page. But again, this information will be characteristic only of the current session. Once you close the browser, all data will be deleted automatically.
Now let's take a closer look at the key functional capabilities of this browser.
Main functions of Epic Privacy Browser
Epic Privacy Browser is a reliable, modern browser that can provide the most convenient, functional and simple work on the Internet while maintaining high levels of privacy, protection from any unauthorized access. Of the main functional capabilities of Epic Privacy Browser, we would like to highlight the following:
- The presence of built-in instant proxies.
- Safe search.
- The Do Not Track option.
Let's consider all these solutions in more detail.
What are the built-in instant proxies of Epic Privacy Browser
How do most modern browsers work? You send your request through the browser to the server. It automatically identifies your IP address, since without this it will not know where exactly it needs to send the answer. In principle, everything is logical and clear here. The system also uses information about the address in order to determine your real location and offer directly local sites, portals in your native language. But, unfortunately, this information is used not only for these purposes.
To maintain your privacy, protect your device from hacker attacks and any other unauthorized access, IP-address must be hidden. This is exactly what Epic Privacy Browser does. In this case, we are talking about the fact that with each of your requests that will be sent to the Internet from your IP address, it will be automatically replaced by a proxy server, so that the network will not be able to identify you as an end user.
To connect such a secure connection, you just need to click on the corresponding icon located to the right of the address bar. That is, the system will see you as a user from another country in the world. We have already said that the Epic Privacy browser uses servers located in 8 countries around the world. It turns out that during the connection process, the fastest option is selected, which will ensure the most stable and efficient interaction for the user. You will also be able to set in the settings those sites with which you would like to maintain direct interaction.
Ensuring safe search
The Epic Privacy Browser has a separate safe search page, which is always marked by the program. This means that it implements the technologies of leading search engines from around the world. However, no specific information about the tools, services, and systems used is disclosed here. In principle, this is all logical, since this is the only way to ensure the preservation of privacy and security of work on the Internet for users.
At the same time, the system does not try to predict your requests by the first letters, does not send data to the server about which key phrases you used to go to a particular resource. This is ensured by connecting proxy servers, which we discussed above.
But Epic Privacy Browser also uses other modern methods to ensure the protection of user information:
- prohibits the loading of cookies, does not use cache;
- blocks advertisements;
- disables services that can track geolocation;
- erases digital fingerprints every time after finishing work;
- blocks all cryptomining options, including those hidden from visual identification.
That is, as soon as you exit the browser, all the information that you left about yourself in the search engine, including browser history, database information and any other residual files are deleted automatically.
Do Not Track Option
We have already talked about that the system itself and individual websites constantly monitor user actions on the network. This is done for various reasons. For example, services that work with advertising buy the appropriate places on sites and then track ad views to understand how effective their decision was, how many customers they managed to attract with such an action.
Web analytics tools monitor unique visitors, count their number, check which pages of the site they visited, how long they stayed on them. This is what allows you to identify the material that is most interesting to users and subsequently offer similar solutions. The presence of social buttons on sites will allow people to quickly and easily share interesting information.
That is, all this was primarily developed to provide modern users with maximum convenience of working on the network and quick search for the necessary information. But, unfortunately, not everything happened as planned. Such information is actively used today to distribute advertising. It is also actively used by attackers to gain access to users' personal devices, launch malicious software on them, etc. It is precisely these actions that have led to the fact that most modern users rely primarily not on ease of use, but on the confidential storage of personal data and their own security.
A technology such as Do Not Track was first used in practice by the Mozilla browser back in 2011, and soon after that it was adopted by other equally popular search engines. And everything would be fine if compliance with this specification was mandatory, not voluntary. That is, most modern advertising networks simply ignore such headers and users are still sent ads that they do not need at all.
The Epic Privacy Browser took a slightly different path here. In particular, it decided to automatically block all those types of tracking and advertising tracking that are used in practice today. If you go to a page where there is advertising, a pop-up window will briefly appear, which will provide information about how many and what elements are blocked by the browser. Moreover, such an action significantly speeds up page loading, since time is no longer wasted on advertising. Is this good or not? For users, yes, it's good, but for the sites themselves, many of which earn quite well on advertising, such blocking, of course, does not inspire enthusiasm.
What are the disadvantages and limitations of Epic Privacy Browser?
Despite its technological advances, fairly deep development and thoughtfulness, the developers of Epic Privacy Browser still failed to eliminate absolutely all the disadvantages and relieve users from limitations in their work. In particular, we are talking about the fact that the browser does not support plugins. What does this mean? That almost all password managers will not work together with the search engine. That is, you will need to enter all the parameters each time you connect.
Relatively recently, a statement was made by the executive director of the project regarding the fact that in the near future a set of basic plugins will be integrated into Epic Privacy Browser, among which there will also be a password manager. But at the moment this has not been implemented yet.
Also, in the process of direct use of Epic Privacy Browser, it was already possible to find out that this browser does not provide access to all sites. That is, resources were found that in this browser either did not load at all, or did not work quite correctly. As an example, when trying to connect to a crossword site through Epic Privacy Browser, the site asked to enter a login and password for access with a proxy server enabled. And it was not possible to solve this problem by disabling certain options directly on the toolbar. As soon as the secure connection was disabled, this problem was solved automatically.
What else should potential users of Epic Privacy Browser know? So, there were cases when the search page here did not support a number of standard modifiers. Most often, this was observed in practice in the case of entering repeated search queries.
So is it worth trying Epic Privacy Browser in work?
Whether it is worth switching from your usual browser to Epic Privacy Browser is a question that each of you must find the answer to on your own. We can say from ourselves that such a solution will be convenient for those who often use the incognito mode in Chrome or other analogs in their work. Yes, there are certain problems, inaccuracies that require professional elimination. But as practice shows, the developer reacts to such things quite quickly and tries to eliminate the shortcomings as soon as possible. That is, Epic Privacy Browser is worth using for those who rely on protecting their personal data when working on the Internet.
To make it easier for you to make the right and informed decision, we have created a separate block with the advantages and disadvantages of this browser.
So, the strengths of Epic Privacy Browser include:
- the presence of a built-in proxy server, which can be activated and connected to work with just one click;
- ensuring high security indicators when surfing the network;
- the presence of a function that cancels GEO-tracking;
- no saving of browsing history;
- automatic deletion of all traces of your activity on the network after finishing work;
- ensuring comprehensive protection of the user's personal data.
Among the disadvantages, we note the lack of compatibility with password managers, although they promise to eliminate this in the near future, incorrect operation of a number of sites, difficulties with the use of some search modifiers. If such restrictions are not particularly significant for you, then you can safely switch to Epic Privacy Browser.
Another point to which we would like to draw your attention is that this browser is initially configured to work exclusively with its own built-in proxies. But will it be convenient for you? You should understand that a large number of users can work on the same proxy server at the same time, which can ultimately negatively affect your personal convenience, Internet connection speed. But you will not be able to connect private proxies directly. But there are other solutions, which we will talk about below.
The sequence of actions for setting up private proxies in Epic Privacy Browser
If the capabilities that the built-in security and privacy protection of Epic Privacy Browser include in practice are not enough for you, then think about using personal proxies. This is what will provide you with the widest possible functionality for working on the Internet, reliable protection from any restrictions, unauthorized access.
Considering the fact that the ability to connect proxy servers directly in this browser is not provided, we suggest performing these works directly through the Windows operating system. We would like to draw your attention to the fact that in this case you will ensure the secure operation of the entire operating system, including all those programs and applications that are currently installed on your computer or laptop.
In order to complete these tasks as correctly and quickly as possible, use our step-by-step recommendations:
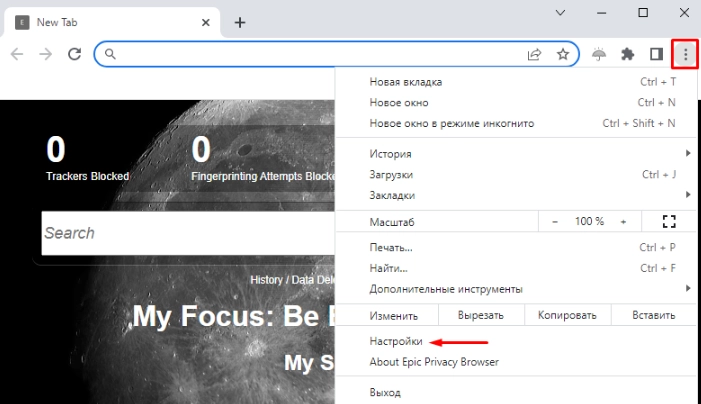
- Install the Epic Privacy Browser on your computer. After completing these tasks, launch it and click on the icon with three vertical dots in the upper right corner of the active window. A list of available options will open in front of you. Here we select the "Settings" tab and click on it.

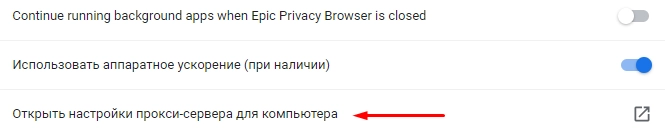
- After that, the program will redirect you to a new settings window. Here, the main options will be presented in a vertical menu on the left side of the screen. We go down almost to the very bottom to such a tab as “System”. We go into it. Again, a new window opens in front of you, in which you need to find such a submenu as “Open proxy server settings for the computer”. Click on it.

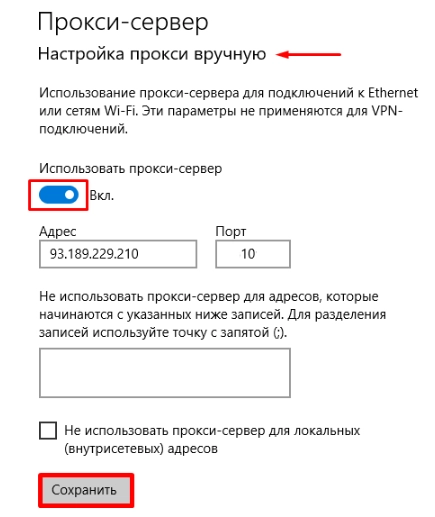
- The program will automatically redirect you to the system settings window. The first thing you need to do here is to move the slider in the "Use proxy server" block from inactive to active. After that, this button will be highlighted in blue and there will be an inscription "ON" next to it. Below, the windows that need to be filled in will become active. In particular, in one of them you need to specify the IP address of your private proxy server, and in the other - its port. If you want to maintain direct interaction with the Internet for a number of sites, you need to insert the corresponding URL address into the last unfilled window. You will also have the opportunity to check the box next to the inscription “Do not use a proxy server for local, intranet addresses”, in order to work with them without a secure connection in the future. We confirm the correctness of the entered information and the desire to activate a private proxy by clicking on the “Save” button.

By and large, all the necessary settings are completed. Now, as soon as you enter a request in the Epic Privacy Browser, a window with proxy server authorization will open in front of you, where you enter the login and password for access, and then click on the "Login" button.
As you can see, there is nothing complicated or incomprehensible in these works. This means that absolutely everyone of you can cope with them without much time, money, or effort. The only thing left to think about here is what proxy servers you will use when working with Epic Privacy Browser.
The best proxies for connecting to Epic Privacy Browser
In order not to risk your own safety, to ensure maximum convenience of working on the Internet, reliable protection from any restrictions from the system, approach the selection of suitable proxies for work as consciously and professionally as possible. If we analyze all these solutions that are presented on the modern market, then the leader here can rightfully be called mobile intermediary servers. They work on the technical capabilities of cellular network operators, provide for use the same IP-addresses that are allocated to smartphone users. This means that the system will simply not notice your connection through a proxy. It will see you as a mobile user. Moreover, such proxies are not blocked, since a huge number of users can fall under restrictions at the same time.
In order not to spend a long time looking for a mobile proxy provider, initially contact the MobileProxy.Space service. This is one of the best solutions in terms of reliability, functionality and price. Among the main advantages we will highlight:
- A huge number of IP-addresses and geolocations from different countries and regions of the world, including for bypassing restrictions established at the legislative level.
- The ability to quickly and easily change the address by timer, having previously configured it in the range from 2 minutes to 1 hour. If necessary, you can also use forced IP change via a link, which will always be relevant in your personal account.
- Simultaneous operation on HTTP(S) and Socks5 protocols, which guarantees high security indicators for work on the network.
- The ability to use mobile proxies for free as part of a two-hour test. This is the solution that will allow you to make sure that the decision you made is correct without any material costs.
- Availability of a 24-hour technical support service that instantly responds to user requests and eliminates all the problems that arise in the work.
You can find out more about all the features of mobile proxies from the MobileProxy.Space service, current tariffs, available GEOs at the link https://mobileproxy.space/en/user.html?buyproxy.
Let's sum it up
We hope that all this information that we have disclosed in our review today will allow you to understand what the Epic Privacy Browser is and evaluate the functionality that you will receive if you decide to use it in practice. We have highlighted its advantages and disadvantages separately so that you can weigh all the pros and cons, and make the right decision.
But we want to draw your attention to the fact that using built-in proxy servers will not always be convenient and reliable, since they are publicly available to all users of the Epic Privacy browser. A much more reliable and proven solution would be to connect private proxy servers, in particular mobile proxies from the MobileProxy.Space service. If you have any additional questions, you can contact technical support or study the relevant material in the FAQ block.