Dynamic mobile proxies
The article content
- how do social networks and major portals recognize bots?
- how does it work?
- first stage of verification. whose ip address are you using?
- second factor. static or dynamic address. which is safer?
- the third factor. what operating system fingerprint are you giving?
- classification
- purpose
- conclusions about mobile proxy
Mobile proxies are gaining popularity more and more. First of all, this is due to the fact that the platform algorithms Vkontakte ,
How do social networks and major portals recognize bots?
Modern social networks use a complex multi-level algorithm based on Fingerprints and behavioral factors based on average user behavior.
At the network level, the following are checked:
- IP
- OSFingerprint
- MTU
- BlackLists
At the program level, you can distinguish:
- Canvas
- WebGL
- Cookie
- Fonts
- Audio Fingerprint
How does it work?
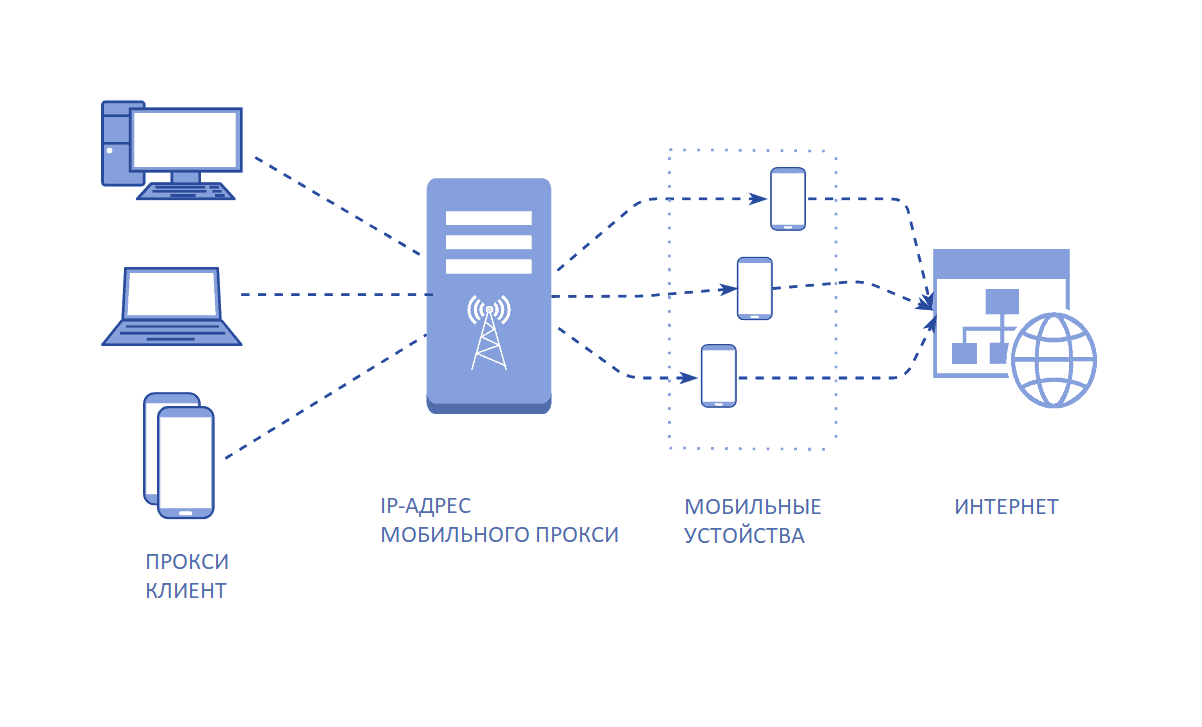
Basically, mobile proxies & ndash; the same as the standard ones, with the only difference that the connection to the network is via a cellular operator. Those. standard proxies allow the user to get anonymity, and dynamic mobile proxies show that he went online through a mobile operator. This is especially true for social networks, which the majority of users visit via mobile devices. And if we talk about Instagram, then there is practically no access from desktop devices.
The main feature of this decision and the argument in favor of buy a mobile proxy : shark IP addresses; the cellular business is rarely used as a proxy. They have very few proxy addresses & ndash; for several million subscribers, there are, at best, several thousand. Therefore, blocking such IPs for social networks is unprofitable & ndash; blocking sanctions would affect not only those using dynamic mobile proxies, but also users of regular proxy servers. Moreover, in the first place it is them that they will touch & ndash; people who are innocent at all will be blocked. Therefore, social networks do not work with IP addresses belonging to key mobile operators. And even if the sanctions are applied in isolated cases, the trust in the IP addresses of the cellular operator is restored quickly. Enough buy a cheap proxy and build it correctly, and you can reduce the number of bans associated with the use of suspicious IPs to almost zero.
First stage of verification. Whose IP address are you using?
Social networks are quite easy to calculate an ordinary proxy, and your account may be blocked, because ordinary users cannot access the network through the IP addresses of cloud servers or hosting providers.
Using a mobile proxy, you connect to the server of the cellular operator. In turn, millions of users access several thousand IPv4-based addresses sent to smartphones using the NAT mechanism. The system will read your IP as a user IP, which will prevent you from being suspected of massive actions at the IP check stage.
If you are blocked, ordinary users will also fall under the distribution. Therefore, the use of a mobile proxy when working with social networks can reduce the likelihood of blocking, since they are not ready to bear reputation losses in the form of an ordinary social network user blocked by mistake.
Second factor. Static or dynamic address. Which is safer?
When buying a regular proxy, you get static IP addresses that do not change throughout the entire work, if you do not do it manually. With a mobile proxy, you get access to dynamically changing addresses. Hence, you get access to the entire address pool. & Nbsp;
The third factor. What operating system fingerprint are you giving?
Another equally important factor is the detection of the proxy operating system fingerprint at the TCP / IP level (Passive OS Fingerprint) and User-Agent verification.
When using a regular proxy, the verification system considers your User-Agent as Linux, since the standard proxy is made using this operating system. Ordinary users leave Android, Windows or OSX as the title. Accordingly, as soon as the verification system notices a discrepancy, you can get a lock.
Classification
First, dynamic mobile proxies can be classified according to the key operators cellular communication & ndash; everyone knows them.
Secondly, there is a classification of mobile proxies by mobile standards & mdash; 3G, 4G, LTE.
Purpose
The main reason to buy a mobile proxy, as seen from the above & ndash; avoid blocking when working on social networks. In addition, dynamic mobile proxies are used for:
- Create multiple accounts on social networks, messaging programs, etc.
- Mass collection of likes, views, subscribers.
- Comment and post.
- Buying traffic for advertisers' website in ad systems.
Sometimes ordinary users also decide to buy mobile proxies in order to maintain confidentiality. You can do this on our website!
Conclusions about mobile proxy
- When working with social networks and large portals, the security of the time and money invested in the project is significantly increased.
- Save you time by not having to deal with a huge list of static IP addresses.
- A regular proxy uses IP addresses that cannot be owned by an individual (hosting providers or cloud services), which can lead to blocking. With a mobile proxy, you connect to the proxy server of the cellular operator. The system will read your IP as a user IP.