Why do we need a chain of mobile proxies
Mobile proxies are increasingly being used to gain access to blocked sites, prevent IP-address bans, ensure multithreaded operation with multiple accounts, form a high level of anonymity and network security. They are characterized by increased reliability, stability and efficiency of work, they allow you to solve many daily tasks for both ordinary users and those who work professionally on the Internet: SEO and SMM specialists, marketers, arbitrageurs, followers, etc. But in some cases, even the most reliable mobile proxies cannot provide 100% efficiency without locks and restrictions. And then the proxy chain comes to the rescue. So what is it about and what opportunities does it provide to users?
The problem of unprotected work on the Internet
To understand how the chain of mobile proxies works, you need to know how, in principle, user access to Internet resources is carried out and what risks it carries. So, any of your actions on the network, whether it's visiting a website, a social network, a game portal, or any online application, will be accompanied by your computer sending a request for interaction. Yes, everything is logical and clear here. But the problem is that in parallel with this request, information about your real IP address is transmitted to the network, a unique code that is assigned to each device connected to the network. And what happens if this personal information falls into the hands of an attacker? An unscrupulous person can easily connect to your computer in order to:
- theft of personal data for your own use or the formation of a customer database, as a result of which you will receive intrusive messages about the purchase of a particular product or service;
- sending malicious software that can completely paralyze the operation of your device;
- conducting their illegal actions through your IP address;
- theft of important documentation, including information about bank cards.
These are only the most common problems that are fraught with unprotected work on the network. And if ordinary mobile proxies minimize all this, then the chain of servers is guaranteed to secure your actions on the Internet.
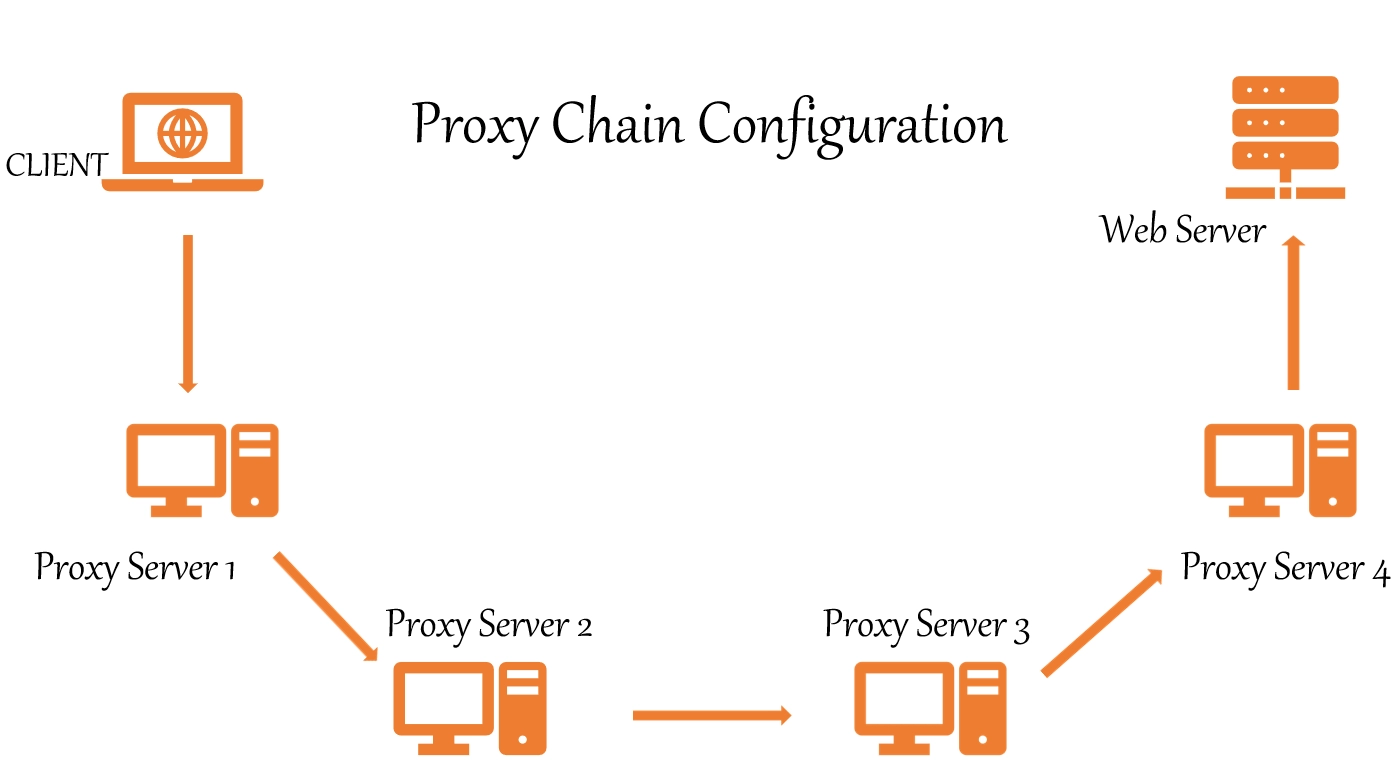
What are server chains
The proxy chain is a connection to the operation of several servers that are connected sequentially to work between the user and the Internet. It turns out that the request you sent will pass through several intermediary points and IP address substitution will be carried out in each of them: you transmit the information to the first server, it to the second, and so on, up to the last in the chain, which will already transmit it to the target site. The reverse transmission of the response is carried out according to the same principle. A similar connection was called "cascade".Using proxy chains in your work, you get:
- Absolute level of anonymity: even the most advanced software is not able to track the entire sequence of IP address substitution.
- The ability to quickly and simply set rules that will allow you to change the geolocation for each site or application.
- Unlimited access to pages to which access is completely closed or special restrictions are provided. This also applies to sites that are blocked both locally and regionally.
- A high level of protection against any kind of unauthorized access, whether it is a virus attack or hacking in order to obtain user's personal data.
- Sufficiently high connection speed. It is provided primarily by data caching and the use of high-speed communication channels by mobile proxies. But we must understand that a long chain length will still reduce the speed of work. And here it is necessary to find the "golden mean" between the level of security and the speed of interaction.
- Automatic blocking of annoying ads. You won't see her at all.
- Hiding geodata. As in the case of an IP address, the site you want to visit will see the location and IP of the server that is last in your chain.
Not all proxy servers can be combined into chains. It is recommended to check this point with the service provider in order to be sure that the purchased product will meet your needs. In particular, here https://mobileproxy.space/user.html ?buyproxy presents to your attention mobile proxies that are great for building chains of any length. This is a multifunctional product that works simultaneously on both HTTP(S) and Socks5 protocols thanks to connection via parallel ports. Each user receives a personal channel with unlimited traffic, the ability to change IP addresses automatically by timer or forcibly through a special link. Rotation by geolocation, cellular network operator is also provided.
Some information about creating proxy chains
One of the most important points in the process of creating a proxy chain is the type of protocol. So, you can combine servers running on HTTPS, SOCKS and CGI protocols into chains. All this is created by users independently using specialized software, the so-called proxy programs. The same chain may include proxies running on different types of protocols. The most difficult thing is to make settings with HTTP servers, and the easiest thing is with CGI:
- To create a chain from an HTTP(S) proxy, you will need to use a software proxy and create a virtual tunnel in it. Next, you will just need to enter the addresses and ports of those mobile servers that you would like to connect to work. You can generate the appropriate document in advance and upload it to the program. The main thing is to tell the program the correct sequence of connection with individual nodes. Prerequisite: support for the same protocol.
- To form a SOCKS proxy chain, you will also need to connect a special program. Alternatively, you can use ProxyChain, HTTPort, SocksChain applications. They are also suitable for working with HTTP(S) servers. The sequence of actions is identical: upload the proxy technical data (IP addresses and ports) to the program in the sequence in which they will be connected to work.
- To configure the CGI proxy chain, you do not need to use additional software. So, it will be enough for you to register the URL of another in the settings of one proxy, click on the "Go" button. And so consistently perform similar actions with other servers. At the very last link in the chain, enter the URL of the site you would like to visit. That's all.
Options for creating proxy chains
To ensure stable operation of the proxy chain, it is necessary to ensure the correct location of each individual link. Otherwise it won't work. So, you can create the following variations of chains from mobile proxies:
- SOCKS proxy — HTTPS proxy — CGI proxy.
- HTTPS proxy — CGI proxy.
- HTTPS proxy — SOCKS proxy.
- SOCKS proxy — HTTPS proxy.
- SOCKS proxy — CGI proxy.
- HTTPS proxy — SOCKS proxy — CGI proxy.
But the chains of such a plan "CGI proxy — SOCKS proxy » or «CGI proxy —HTTP proxy » will not work.
Now you know why proxy chains are needed and how to configure them correctly. One important question remains: how many servers should be connected to work sequentially to ensure a decent level of anonymity and work security, but not at the expense of connection speed? For normal operation, two intermediary servers will be enough. It was left to the small – to go to the MobileProxy service website.Space to purchase reliable mobile proxies in the right quantity and on the most favorable terms.