What you need to know about DDoS attacks and how to resist them

The article content
The modern Internet is a place where users find useful information, entertainment content, work, develop their own business, promoting goods and services. But there is also a fairly large number of threats and potential dangers concentrated here, which may affect individual users and their personal devices, local and corporate networks, server equipment, any sites, services and other online platforms. In particular, for the latter, one of the most pressing and serious problems will be distributed denial of service attacks, namely DDoS attacks.
In this case, we are talking about such actions of attackers that are aimed at overloading the system, which makes target sites and services inaccessible to the user audience. Such an impact has extremely negative consequences for business. If the site does not work, then even a loyal audience leaves it, which means that the business loses customers and, accordingly, income. As a result, financial losses become so large-scale that the company's further work on the market is in great question.
Today, a fairly large number of types of DDoS attacks have been identified, but the most common here are those types of impact that occur at the transport layer and application layer. In the internal classification, they are marked as L4 and L7. Often, an L4 DDoS attack is also combined with an impact of the L3 network layer. Is it possible to provide protection against this? It is possible, if you have a good understanding of this issue, understand the key differences between different types of DDoS attacks and know what methods can be used to minimize such threats. It is these issues that we will dwell on in more detail in today's review.
Now we will consider in detail what a DDoS attack is, highlight the main classifications of such impacts and get acquainted in detail with the most common options. We will provide the main methods that modern attackers use in practice. Let's get acquainted with advanced DDoS protection technologies that each of you can adopt to ensure high security rates for various online sites and services.
What is a DDoS attack and its classifications
DDoS attack is an abbreviation for Distributed Denial of Service Attack, which literally translates as a distributed attack of the "denial of service" type. Its goal is to provoke a denial of service of a user request on the server side or any other electronic resource. The site or service is overloaded so much that it simply ceases to be available to users. In most cases, it is implemented by sending a very large number of malicious chaotic requests from devices with different IP addresses. The attackers manage to implement this idea in practice thanks to the presence of vulnerabilities in the existing security system of the online platform.
As a result of such an impact, traffic and load increase significantly, limits and bandwidth resources are reduced to zero. As a result, the server cannot process such a number of simultaneously incoming requests and, in response to the user's request, returns the 5xx code, which implies a denial of service. The closest analogue of a DDoS attack is DOS. Here the principle of action is identical, the only difference is that in the case of a DOS attack, all actions are carried out from one device.
Today, DDoS attacks are classified by 2 key parameters:
- By nature of use.
- By level of network model.
Now we will consider both types of classifications in more detail.
Types of DDoS attacks by nature of use
Depending on what idea the DDoS attack is used to implement, the following types of such impacts are distinguished:
- Excessive filling of the Internet channel. Involves sending a large number of malicious HTTP requests over a fairly long period of time. As a result, the server's channel capacity begins to decrease down to zero, and the incoming traffic limit set by the hosting provider is exhausted. After this, the server is automatically blocked. In some cases, it can switch to another pricing option, which involves additional payment for each overused megabyte of traffic.
- Exploiting errors and vulnerabilities in the code. During such an attack, the attacker selects a separate section of the code and subsequently affects it. As a result, either the server or the electronic resource is disabled. This is a kind of hacking.
- Increased load on server resources. During such an attack, the hacker identifies the weak points of the electronic resource and affects them directly, sending a huge number of illogical requests. Mostly, all sorts of forms of sending data, search fields on websites and other elements are used, the level of protection of which leaves much to be desired. As a result, if the server is weak, insufficiently protected, if there are discrepancies in its configuration, it simply turns off, that is, “falls” or, as they say, “lies”.
Types of DDoS attacks by network model level
Depending on the network model level, the following types of DDoS attacks are distinguished:
- Link layer L2 attacks. They involve flooding hubs and switches with data packets, which are used at the data transmission stage.
- Network layer L3 attacks. They are aimed at exhausting network traffic with flooding and reducing throughput.
- Transport layer L4 attacks. Attackers fill TCP/UDP data transfer protocols with garbage traffic.
- Session layer L5 attacks. Their essence consists of creating a huge number of malicious empty sessions that will be launched via the Telnet protocol.
- Presentation layer L6 attacks. In this case, a massive number of requests will be sent via the SSL protocol.
- Application layer attacks. Here, attackers send a huge number of simultaneous requests via the HTTP protocol.
Above, we talked about the fact that in practice today, the most frequently used DDoS attacks are transport L4 and application layer L7, and a combination of the network and transport layers, i.e. L3 and L4, is also possible. It is these impacts that we will dwell on in more detail further in today's review.
What can be the consequences of DDOS attacks
We have already mentioned above that DDOS attacks are something that can cause serious damage to your business and even lead to a complete shutdown. If your online presence is subjected to such an impact, then its consequences can be as follows:
- Unavailability of the site, service for the user audience. Under the influence of numerous requests, the server refuses to provide service. It simply cannot withstand such a load. As a result, Internet users simply cannot access it. All server services and related components also remain paralyzed. And this will continue until the attack stops. As a result, clients are lost, the process of site administration becomes significantly more complicated.
- Partial or even complete loss of data, damage to server components. Serious DDOS attacks can cause information leakage and disable components of your system. Modern attackers often launch other, much more serious attacks under the guise of DDOS, which often leads to a complete hack of the server and leakage of confidential information. There is a chance to restore and return the site to working condition, but it will require quite serious time and material costs both for restoration and subsequent maintenance.
- Deterioration of the business reputation, decrease in the website rating and its position in search results, decrease in trust and loyalty from the consumer audience. If your customers cannot access the site, if they see an error every time they try to connect, they will quickly simply switch to your competitors and order the goods and services they need from them. The same applies to potential business partners and even search engines. As a result, your business suffers not only financial but also reputational damage, the effectiveness of website promotion in search results is minimized.
Before launching a DDOS attack, attackers often conduct preliminary reconnaissance. For these purposes, they use open sources of OSINT (Open Source Intelligence). Here, the limits of the electronic perimeter are studied, inputs and outputs are identified, all ports or key nodes are scanned, backend and frontend segments are checked, the database, source code, and connected accounts are checked. During such preparatory activities, attackers manage to identify shortcomings and weaknesses in the operation of your security system, obtain maximum information about your site, and systematize it according to various parameters. This is what will allow them to build the most effective strategy for a subsequent attack.
From this, one simple conclusion can be drawn: the greatest vulnerability to DDOS attacks will be for sites and any other electronic resources that are not updated in a timely manner, are not administered, and are not subject to high-quality optimization. This also includes services whose configuration is not ideal. This means that if you eliminate all these problems, you can significantly increase your resistance to such impacts. Most DDOS attacks are launched for the purpose of blackmail or revenge. They are used by unscrupulous competitors, including when conflict situations arise in business. Recently, they have also become a key element of cyber warfare.
Now let's move on directly to getting acquainted with what DDOS attacks of the network L3 and transport layer L4 and application layer L7 are.
DDOS attacks of the network and transport layer
DDOS attacks of the network (L3) and transport layer (L4) are aimed at providing an excessive load on network equipment or transport protocols, mainly UDP and TCP, thereby disrupting the stability of the system. They lead to increased consumption of network resources, which will cause blocking, failures and the inability to access official websites or business services. In particular, very often overload is observed in firewalls, routers, balancers.
Despite their diversity, transport-level DDOS attacks are quite easy to identify. Moreover, they can be blocked already at the network infrastructure level, which allows you to build a good counteraction system. But you should understand that very often attacks at the L4 or L3 level are just a distraction before a more serious impact. They are often launched before using DDOS at the L7 level or to overload the system before launching other malicious actions.
All DDOS attacks that can be performed at the network and transport levels can be divided into 2 separate categories depending on their type:
- Protocol.
- Valumetric.
Let's consider both options in more detail.
Protocol attacks
Protocol DDOS attacks are carried out at the L3/L4 levels. The main goal here is to exhaust the resources of network equipment that participate in packet data processing. The attacker sends packets with malicious content to the server and does not allow packets coming from regular users to be processed.
The following types of attacks are used in this case:
- SYN flood. The attacker sends a huge number of SYN requests to establish a connection, but the connection process is not completed. As a result, the service resources are very quickly depleted, since it is forced to constantly maintain the connection without completing it.
- TearDrop Attack. This is an attack with fragmented packets. The hacker sends fragmented packets with data to the victim's server. That is, large files are transferred in parts, and the server must collect them into one large packet during the receiving process. But the hacker makes it so that the packets are shifted relative to each other, they are mixed up, and the server is unable to determine the sequence in which they should be connected. As a result, the equipment spends a lot of resources trying to assemble the file, while requests from regular users go unserved.
- Smurf Attack. In such an attack, the hacker changes his IP address to the IP of the device that he is targeting, and then sends a large number of requests to different devices connected to the network. When they receive them, they send responses, but to a fake sender. As a result, a fairly impressive incoming traffic is generated for one IP address, which leads to problems in operation.
Volumetric attacks
Volumetric DDOS attacks are a volumetric impact that is also carried out at the network and transport level (L3/L4). They are aimed at depleting the bandwidth of the communication channel by sending a large number of illegitimate requests. In this case, the following types of attacks can be used:
- UDP flood. Huge UDP packets are launched to random service ports, which overloads its traffic processing system and causes complete exhaustion of bandwidth.
- ICMP flood. This attack uses the ICMP protocol, through which a huge number of echo requests (ping) are sent. Most of them are not about transmitting data, but about sending messages about certain system errors. As a result, the server is forced to give such an echo response, thereby showing that it is operating in normal mode. As a result, an increased load is still created on network devices, which causes failures in operation.
- DNS Amplification. Hackers carry out such an attack by sending a large number of corresponding requests to a selected DNS server using public DNS resolvers. But the settings here will no longer be correct. As a result, the server must provide larger responses, sending them to the IP address of the "victim". As a result, the server becomes heavily overloaded and unavailable.
Application-Level DDOS Attacks
L7-level DDoS attacks are aimed at exhausting the resources of the application and Internet servers. This in itself makes them more difficult to identify. Such attacks are very similar to regular user traffic, and the main task is to create an excessive load on services using requests that require increased computing power at the processing stage. The result will be such that regular users will have to wait a long time for responses from services, or will not be able to access them at all.
One of the main difficulties in this case is the problem with identification, since such a connection looks quite natural for the system. Their detection requires the use of advanced traffic analysis systems, as well as the most comprehensive and accurate understanding of how applications work in principle. Only with this knowledge can you effectively protect yourself from such attacks.
Today, attackers use the following types of applied DDOS attacks:
- HTTP flood. During this type of attack, hackers send a large number of HTTP requests to the web service. As a result, the device is forced to process them, which takes a lot of time and leads to noticeable delays, and in some cases, to a complete shutdown of the resource. Using a large number of fairly heavy POST requests, the attacker overloads the server so much that sites and services become inaccessible to the average user.
- SQL injection. Offers the use of malicious SQL commands. They are embedded in the requests that will be sent to the databases, thereby forcing them to perform unauthorized actions. In this case, we are talking about changing the data itself or gaining access to classified information, including bank details and other sensitive data.
- Slowloris. This is a session attack that involves simultaneously launching a large number of HTTP sessions and maintaining each of them in an active state for a fairly long period of time. As a result, this leads to a noticeable slowdown in the operation of servers, or even their complete failure. As in other types of similar attacks, real user requests are left without service.
- XSS attacks. In this case, attackers use vulnerabilities that exist on a particular Internet page. They will become the place for the subsequent introduction of malicious code. As a result, this opens up the possibility for hackers to gain access to personal user data and other sensitive information. The consequences of such impacts are extremely unpredictable, but nothing good can be expected in this case.
- SSL/TLS flood. In this case, the hacker sends a huge number of incorrect requests to the target server protected by SSL and TLS protocols. As a result, the server is forced to spend its own resources on forming a TLS session, exhausting them so much that the obsservicing of real users is not performed. Here it is necessary to understand that the processing of encrypted SSL/TLS packets in itself requires much more time than normal ones. That is, even in legitimate mode, the server is overloaded. But if many of them are launched, the delays can be very serious.
This category also includes DDOS attacks aimed at specific functions. In this case, attackers can choose vulnerabilities in the logic of software products as an object, which will ultimately lead to problems with the operability of individual functions, or even provoke a service shutdown.
A brief comparison of L3/L4 and L7 DDoS attacks
For greater convenience in perceiving the presented higher information on the most common types of DDOS attacks today, we have prepared a brief summary table.
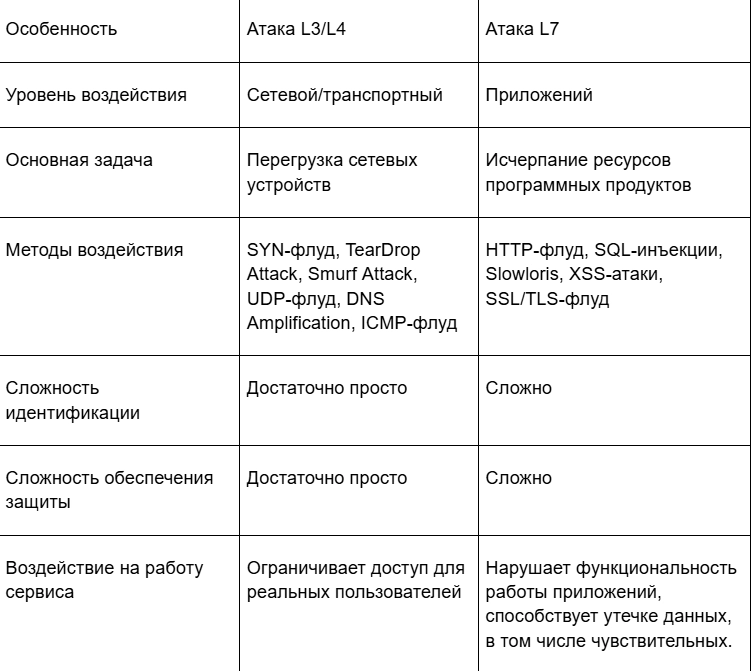
As you can see, attackers launching DDoS attacks have quite a few options. And no one can tell you in advance which of these methods will be applied to your resource. This means that in any case, you need to prepare for potential impact and ensure that your resources can withstand, maintaining their functionality and operability for real users. This means that you need to pay due attention to the formation of protection against DDoS attacks.
What technologies should be used to ensure protection against DDoS attacks
Considering the fact that the modern IT technology market is well aware of the problem of DDoS attacks, there are many ways to counter them. Thus, all technologies presented in this market segment can be divided into separate groups. In particular, we are talking about the following solutions:
- Local methods of protection against DDoS attacks. Such technologies are also called on-premise. In turn, they are classified into software and hardware. The latter involve the use of specialized network devices. These solutions can be installed both by the users themselves and by providers. Most local solutions are used in practice by large telecom operators. This includes both cloud and Internet providers, as well as data centers. These are the categories of users who can afford to maintain a full-fledged personal response service, thereby coping with fairly powerful attacks that involve the launch of hundreds of gigabytes of data. Moreover, they can offer their own services to other clients, receiving additional income from this.
- Cloud methods of protection against DDoS attacks. This technology is implemented in almost the same way as a local solution. But along with the packet protection itself, cloud service providers also offer additional services to protect services from attacks carried out by intruders using bots. In this case, the HTTP protocol is used. As additional services, cloud providers offer technical support and comprehensive support directly during the attack itself. This solution will be optimal for most modern companies, regardless of the niche they operate in and sales volumes.
- Hybrid methods of protection against DDoS attacks. Here we offer a set of solutions based on local protection methods, but with the addition of a subscription to a cloud service. The latter will be connected automatically as soon as the attack itself is identified. Thanks to the hybrid approach, the disadvantages that are typical for local protection methods are eliminated, in particular volume limitations, and the advantages of both options are combined. In practice, hybrid methods of protection against DDoS attacks are mainly used by large enterprises, those who pay enough attention to ensuring effective interaction with the user and client audience through online communication channels. They are also used in practice by small service providers.
- Using the OSI model to protect against DDoS attacks. This technique will be effective when affecting the network, transport and application levels. But the means of protection will be selected depending on which resources need to be closed from the actions of intruders. Alternatively, filtering the packet of the transport and network layers will provide protection for network devices. Protection from packet flooding is necessary to ensure stable operation of sites. This technique is also used to protect against more serious attacks, including flooding at the L3 - L7 levels, as well as fairly intelligent attacks using specially trained bots with increased resource intensity. As a result, it is possible to protect even critical services and online platforms.
- Symmetric and asymmetric methods of protection against DDoS attacks. Such a classification implemented depending on the connection format. Symmetric protection involves installing a special filter that will pass through both incoming and outgoing server traffic or service information about this traffic. Asymmetric protection methods involve analyzing only incoming traffic. They are more complex to implement, but in practice they have not become very widespread, since outgoing traffic is not analyzed here, that is, there is no complete filtering of attacks. Despite the fact that symmetric protection tools are more expensive, they are still used in practice much more often due to their high efficiency. But here you also need to understand that the signal delay will be higher, since both incoming and outgoing traffic is analyzed.
To select a DDoS attack protection format that will be most effective in your case, you need to take into account the specifics of the business, the features of online representations. In practice, a combination of different options is often used, which allows you to get the maximum result and prevent unauthorized actions by intruders.
Summing up
We hope that the information presented above has allowed you to understand how serious a threat DDoS attacks pose to various online platforms and to choose the most effective methods of protection for yourself. In most cases, the optimal solution will be multi-level systems that include both network and application technologies. It is also important to organize regular monitoring of the operation of your online presence, constantly update the security system. Only by combining hardware and software techniques, using advanced hybrid solutions will you be able to protect yourself from DDoS attacks and ensure stable operation of all systems.
Mobile proxies from the MobileProxy.Space service, among other things, will also provide significant assistance in implementing these ideas. At the link https://mobileproxy.space/en/user.html?buyproxy you can get acquainted in detail with the functionality of this solution, current tariffs, available geolocations and other points that will allow you to be convinced of the prospects of using such intermediary servers in practice. It is also possible to use a free test for 2 hours to make sure how easy to use this product will be.
The most popular questions on the topic of mobile proxies and professional answers to them can be found in the FAQ block. Also, at any time, you can contact the technical support specialists working around the clock for additional advice and assistance.