Port forwarding
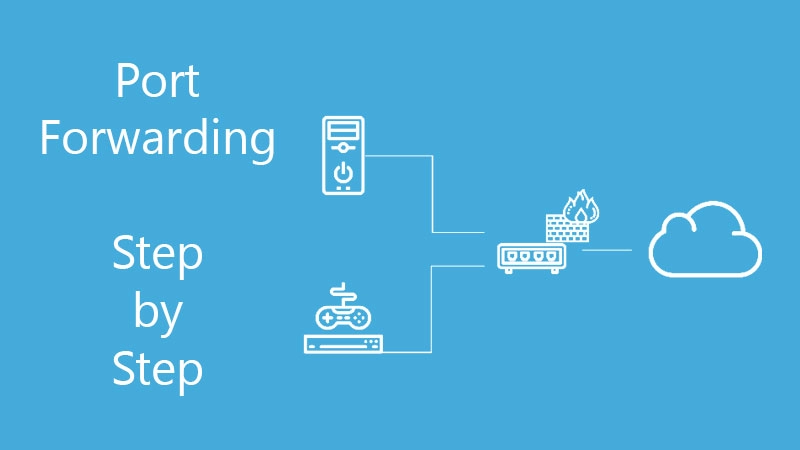
In computer networks, port forwarding or port mapping is a network address translation (NAT) application that redirects a communication request from one combination of address and port number to another, while packets pass through a network gateway such as a router or firewall. This method is most often used to create services on a host located in a secure or masked (internal) network accessible to hosts on the opposite side of the gateway (external network) by reassigning the destination IP address and communication port number to the internal host.
Why do I need port forwarding?
Port forwarding allows remote computers (for example, computers on the Internet) to connect to a specific computer or service on a private local area network (LAN).
In a typical residential network, nodes access the Internet via a DSL or cable modem connected to a router or network address translator (NAT/NAPT). Hosts on a private network are connected to an Ethernet switch or communicate via a wireless LAN . The external interface of the NAT device is configured to a public IP address. On the other hand, the computers behind the router are invisible to hosts on the Internet, since each of them only interacts with a private IP address.When configuring port forwarding, the network administrator allocates one port number on the gateway for exclusive use to communicate with a service on a private network located on a specific host. External hosts need to know this port number and gateway address to communicate with the internal network service. Often port numbers of well-known Internet services, such as port number 80 for web services (HTTP), are used for port forwarding, so shared Internet services can be implemented on hosts in private networks.
Typical applications include the following:
- Starting a public HTTP server on a private LAN
- Allowing Secure Shell access to a host on a private LAN from the Internet
- Allowing FTP access to a host on a private LAN from the Internet
- Launching a public game server on a private LAN
Administrators configure port forwarding in the gateway operating system. In Linux kernels , this is achieved by using packet filtering rules in the iptables or netfilter kernel components . BSD and operating systems href="https://mobileproxy.space/en/pages/kak-nastroit-rabotu-cherez-mobilnye-proksi-na-macos.html">macOS before Yosemite (OS 10.10.X) implement it in the Ipfirewall module (ipfw), and macOS operating systems, starting with Yosemite, implement it in the Packet Filter module
When used on gateway devices, port forwarding can be implemented using a single rule for converting the destination address and port. (In Linux kernels, this is the DNAT rule). In this case, the source address and port remain unchanged. When used on machines that are not the default gateway on the network, the source address must be changed to the address of the translator machine, otherwise packets will bypass the translator and the connection will not be established.
When port forwarding is implemented by a proxy process (for example, in application-level firewalls, SOCKS-based firewalls, or through TCP proxy channels), no packets are actually broadcast, but only data is proxied. This usually results in changing the source address (and port number) to the proxy machine address.
Usually only one of the private hosts can use a specific redirected port at the same time, but sometimes a configuration is possible that allows you to distinguish access by the source address of the source host.
Unix-like operating systems sometimes use port forwarding, where port numbers less than 1024 can only be created by software running on behalf of the root user. Running with superuser privileges (for port binding) can be a security risk for the host, so port forwarding is used to redirect a low-numbered port to another high-numbered port, so that the application software can run like a normal operating system. a system user with limited privileges.The Universal Plug and Play Protocol (UPnP) provides the ability to automatically install port forwarding instances on home Internet gateways. UPnP defines the Internet Gateway Device Protocol (IGD), which is a network service by which an Internet gateway announces its presence on a private network through a Simple Service Discovery Protocol (SSDP). An application providing Internet services can detect such gateways and use the UPnP IGD protocol to reserve the port number on the gateway and force the gateway to forward packets to the listening socket.
Types of port forwarding
Port forwarding can be divided into the following specific types: local, remote and dynamic port forwarding.
Local port forwarding
Local port forwarding is the most common type of port forwarding. It is used to allow a user to connect from a local computer to another server, i.e. securely forward data from another client application running on the same computer as the Secure Shell (SSH) client. By using local port redirection, you can bypass firewalls that block certain web pages.
Connections from the SSH client are redirected through the SSH server to the intended destination server. The SSH server is configured to redirect data from the specified port (local to the host on which the SSH client is running) through a secure tunnel to a specific host and destination port. The local port is on the same computer as the SSH client, and this port is the "forwarded port". On the same computer, any client that wants to connect to the same target host and port can be configured to connect to the port being redirected (rather than directly to the target host and port). After this connection is established, the SSH client listens on the port being redirected and forwards all data sent by applications to this port through a secure tunnel to the SSH server. The server decrypts the data.
On the command line, «-L» indicates the local port forwarding. You must specify the target server and two port numbers. Port numbers less than 1024 or greater than 49150 are reserved for the system. Some programs will only work with certain source ports, but in most cases you can use any source port number.
Some options for using local port forwarding:
- Using local port forwarding to receive mail
- Connect from your laptop to the website using an SSH tunnel.
Remote port forwarding
This form of port forwarding allows applications on the server side of a Secure Shell (SSH) connection to access services located on the SSH client side. In addition to SSH, there are proprietary tunneling schemes that use remote port forwarding for the same general purpose. In other words, remote port forwarding allows users to connect from the tunnel server side, SSH or another, to a remote network service located on the tunnel client side.
To use remote port forwarding, you need to know the destination server address (on the tunnel client side) and two port numbers. The selected port numbers depend on which application will be used.
Remote port forwarding allows other computers to access applications hosted on remote servers. Two examples:
- An employee of the company hosts an FTP server at home and wants to provide access to the FTP service to employees using computers at the workplace. To do this, an employee can configure remote port forwarding via SSH on the company's internal computers by specifying the address of his FTP server and using the correct port numbers for FTP (standard FTP port TCP/21).
- Opening remote desktop sessions is a common application of remote port forwarding. Using SSH, this can be done by opening the computing port of the virtual network (5900) and enabling the address of the target computer.
Dynamic port forwarding
Dynamic Port Forwarding (DPF) is a method of bypassing a firewall or NAT on request using holes in the firewall. The goal is to allow clients to securely connect to a trusted server that acts as an intermediary to send/receive data to one or more target servers.
DPF can be implemented by configuring a local application, such as SSH, as a proxy server SOCKS, which can be used to process data transmission over a network or over the Internet. Programs such as web browsers must be configured individually to route traffic through a proxy server that acts as a secure tunnel to another server. As soon as the proxy is no longer needed, the programs should be reconfigured to their original settings. Due to manual DPF requirements, it is used infrequently.
Once a connection is established, the DPF can be used to provide additional security for a user connected to an unreliable network. Since the data must pass through a secure tunnel to another server before it is redirected to the original destination, the user is protected from packet listening that may occur on the local network.
DPF is a powerful tool with many applications; for example, a user connected to the Internet via a cafe, hotel or other minimally secure network can use DPF to protect data. DPF can also be used to bypass firewalls that restrict access to external websites, such as corporate networks.